Introduction
There’s not much good I can say of Edward Snowden except that to his credit, his document releases served as a wake-up call to all manufacturers, service providers, and the average American. So, the NSA is performing wide-scale surveillance; is that really something new? Does anybody remember ECHELON, from back in the early 2000s? This was originally designed for SIGINT (Signals Intelligence) operations but morphed into COMINT (Communications Intelligence) later on in its program life. The program participants were a collective of five nations, also known as Five-Eyes. These are the US, UK, Canada, Australia, and New Zealand.
The truth of the matter is that wide-scale government surveillance was known, although not widely, within the Telecom industry. This followed the disastrous events of 9/11. Consider the following actions:
Actions
1) The first casualty was the nationwide ban on ATM (Asynchronous Transfer Mode) User-Mapped VPI/VCI pairs (Virtual Path ID/Virtual Channel ID). One could ask themselves why the government would do that? There certainly wasn’t any shortage of them. This also came around the time that the FCC started voluntary disclosures (“incentives”) of ATM logical circuit mappings to the FCC. Really, why on Earth would the FCC care about logical VPI/VCI channel maps?
Coincident to that time period, many States approved rate increases for the incumbent phone carriers. In late 2003, for instance, the Florida legislature approved rate hikes of $5/mo for Verizon, $3.50/mo for Bellsouth, and $7.00/mo for Sprint. There are those that believe that this was the NSA’s price of admission. That sounds pretty plausible, as these types of Government incentives have happened in the past. A flat-out fee would be too noticeable, if not illegal. No, the “gift that keeps on screwing” is more a phone company’s style.
2) Armed with logical circuit mappings, entire ATM circuit paths can be rerouted to the closest NSA monitoring station for analysis. And nobody would be the wiser. Mere mortals *might* notice that one day, XYZ router is 25mS away and the next day, 55mS away. How does that happen?
Today, these “voluntary” PVC (Permanent Virtual Circuit) mapping programs continue to exist between the Federal Communications Commission (FCC) and the local phone companies. They seem to happen every few years or so. The following are the two types of “cells” that are used within Asynchronous Transport Mode networks. You can reroute these cells without any user or other Tier 2 carrier entity knowing about it. The UNI refers to the “User Network Interface”. This is what a customer might transport over a fiber-optic SONET (Synchronous Optional NETwork). The NNI cell structures refers to the “Network to Network Interface” that exists over long-haul facilities:
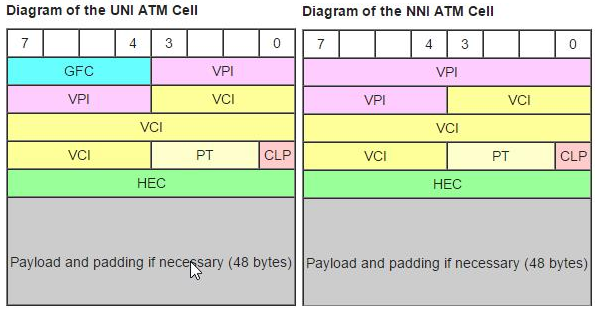
Note that an ATM cell consists of 53 bytes. Five bytes are used for header information, leaving 48 bytes available for data. Yes, it is an awful lot of overhead, but these systems run at extremely high speeds.
3) By 2005, there were actual hallway “whispers” of bulk NSA data collection activities. Along with them came the US Government ban on “dark fiber”. Dark Fiber is raw, “un-lit” fiber-optic pairs between endpoints. The unexpected result of this caused the death of most CLECs (Competitive Local Exchange Carriers). Without the ability to interconnect their facilities with un-lit fiber pairs, the CLECs were forced to use the incumbent Local Echange Carrier “lit” fiber ATM services. Since fiber access isn’t regulated as Unbundled Network Elements (UNEs), the local incumbent carriers simply priced CLECs out of existence. One of the few CLECs left standing is CenturyLink, which acquired fiber SONET rings in this area from KMC Telecom and Level3. I like the term “whisper“. Whispers are all around us. You just have to listen.
4) A short time later, telecom professionals became aware of NSA’s interest in fine-grained DWDM (Dense Wave-Division Multiplexing). We now know, as a result of the Snowden disclosures, that this was a *part* of the aptly-named PRISM project. The NSA is a remarkable collective of brainpower. They understood, and predicted, that there would be long-haul IP-only transmission systems (Non-ATM facilities) between hubs and Central Offices. There is no easy way to reroute that kind of traffic.
The NSA today likely uses a combination of both ATM PVC routing and their PRISM fiber monitoring programs to keep an eye on things. That is the current telecommunications infrastructure here in the United States. I’m quite sure that the NSA, for the most part, will suck in, inventory, and categorize every scrap of information it can about ANYONE. Powered by Big Data and information correlation systems (Big Data Analytics) like IBM’s NORA service (Non-Obvious Relationship Awareness) program, Intelligence Analysts have a remarkable amount of information at their fingertips. For instance, Analysts can view what passwords Jared is likely to use, what restaurants he frequents, where he travels to, who he calls, what websites he’s used, etc. This is largely used for predictive purposes, and is pretty well illustrated in the Hollywood movie about Snowden.
IBM developed the first Enterprise Architecture (EA) Framework in 1986. In 1987, this was basically repackaged with a consortium of other companies, like CSC, DEC/HP, Hammer and Company, Clorox, American Express, Westinghouse, NCR, Texaco, Metropolitan Life, Pacific Gas, Ontario, Hydro, Rockwell, American Express, Banker’s Trust, and others. This was called the PRISM Architecture Framework (Partnership for Research in Information Systems Management). Ironically (or not), this Enterprise Architecture Framework had a limited audience.
Enterprise Architecture Frameworks
There are a lot of EA frameworks in existence today with various acryonyms, such as GERAM, TOGAF, IAF, CLEAR, OBASHI, DNDAF, IFW, ARCON, TRAK, EABOK, MEGAF, SAM, NISTEAM, AGATE, PEAF, TEAF, FDICEAF, GEA, FEAF, MoDAF, DoDAF, NORA, among others. Most of these, but not all, rely on Big Data Analytics. So, at a minimum, the three “V”s of Big Data apply: Volume, Velocity, and Variety. Depending upon what Big Data expert one talks to, there is often up to two more “V”s applied: Veracity (trustworthiness) and Value.
The following diagram represents an EA framework adopted by the National Institute of Standards (NIST):
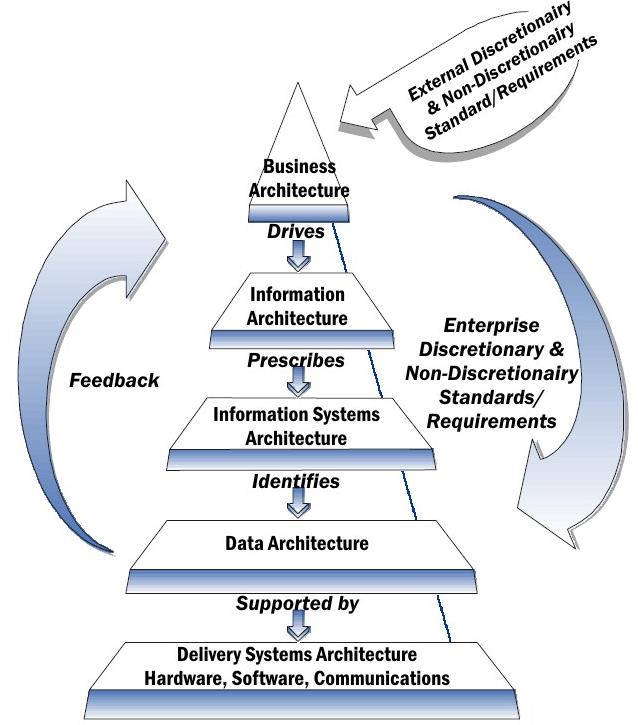
When I do Security Modeling for customers (usually HIPAA/HITECH and PCI/DSS compliance) I use a similar Top-Down approach. This allows for more accurate Threat Vector Analysis.
Conclusion
1) Snowden, the government, whose lack of oversight resulted in excessive surveillance powers, has made you a pariah. Did you really expect something else? The American public, for what it is worth, doesn’t care that much for privacy anyway. You handled your ethical conflict in a very poor fashion, received some bad advice, and now you find yourself in exile in Russia.
2) I believe the average American WILL NOT SEE a decrease in surveillance techniques used by the Federal Government; even if privacy laws are passed in favor of the American consumer.
3) It is safe to say that if traffic is sent insecurely through any commercial carrier, it is subject to interception. The ultimate responsibility lies with the consumer to protect their privacy. Use encryption between any two network endpoints. Use encryption Apps on your Cell Phones to protect both SMS/MMS (Short Message Service/Multimedia Message Service) messaging and telephone calls.
October 22, 2019 @ 6:36 pm
Hello Mr. Snowden. The reference to PRISM is incorrect – it was a privately funded group led by Michael Hammer, Thomas Davenport, and James Champy. They were the ones that created the PRISM Architecture Framework, and IBM nor any of the other funding companies had anything to do with its development. Please read the original research article that uncovered this framework – Journal of Enterprise Architecture, Nov 2013, The PRISM Architecture Framework-Was It the Very First Enterprise Architecture Framework?, Rivera, R.