First observed in February the WannaCry, or WannaCrypt, virus is wreaking havoc in European networks. Major outbreaks of a new variant were first detected Friday, 5/12/2017 in Spain but it has now traveled to over 99 countries. It also took out England’s National Health Service (NHS). The virus is web-based and spreads from users clicking on a bad link in an Email, infected website, or even DropBox accounts.
Once a machine becomes infected, it seeks out other computers to encrypt on the network using a flaw in the SMBv1 (Server Message Block, version 1) protocol. This is the protocol used for File and Print sharing. This flaw was nicknamed “EternalBlue” by the NSA and revealed to the world in the Shadow Broker dumps in April 2017. Ironically (or not, there is a lot of debate about this), Microsoft fixed this bug, detailed as CVE-2017-0147 in March 2017, a month earlier and documented the fix in Microsoft Security Bulletin ms17-010. Ideally, you want to disable SMBv1 altogether, but it is not as easy as it sounds.
Once a “flawed” (EternalBlue) machine is found on the network, the virus installs another delicious file from the Shadow Brokers called “DoublePulsar“. This plugs itself into the standard File Sharing TCP/IP port 445 and allows the hacker to perform RCE (Remote Code Execution) and take over the machine. Sadly, any Windows command or service that runs as “System” can potentially be targeted for privilege escalation.
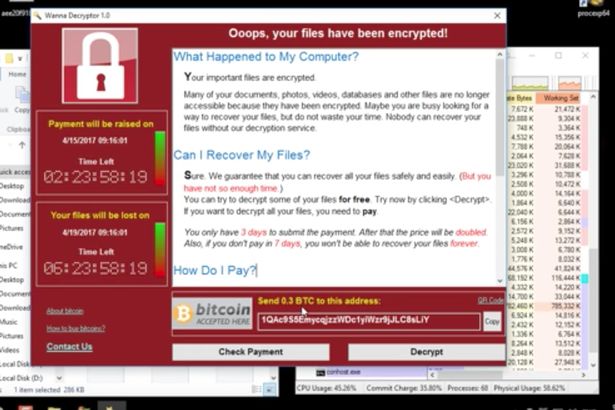
The targeted machines then start encrypting files. They leave the traditional RansomWare demand letter on the screen. There is no decryptor available for WannaCrypt. You must restore from backups. The Windows SMBv1 fixes do not protect against initial intection, only against machines on the local network that are already infected. If you have this virus, the best thing to do is power off the machine, then reload the Operating System in an offline environment.
One of the original instances of WannaCrypt came via a hyperlink called “WannaCrypt by ESET”. Naturally, ESET has protection against this RansomWare. Other antivirus programs that stop this virus are Bitdefender and Kaspersky.
The following are the Microsoft advisories and Security Bulletins regarding their SMBv1 fix:
The WannaCry, or WannaCrypt, RansomWare virus first appeared in February 2017. But this RansomWare has bee spreading like wildfire throughout Europe and has shut down
The company, in a blog post, said WannaCry (also known as WannaCrypt) would attempt to install via a backdoor leaked by the Shadow Brokers called DoublePulsar. If the backdoor wasn’t resident on a target Windows PC, it would then attempt to abuse a flaw in the Microsoft operating system’s Server Message Block (SMB), a network file sharing protocol. “This is the cause of the worm-like activity that has been widely observed across the internet.”
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-0147
- https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
This is an interesting write-up from a potential hacker. It shows how easy it is to use these packages created by the NSA; and all for the low, low price of ZERO!
As I mentioned earlier, there are two versions of the SMB file/print-sharing protocol in every version of Windows 7 and later, along with Server 2008R2 and later. SMB Version 2 offers significant file transfer improvements including differntial transfers, compression, better caching, encryption, as well as being multi-threaded. But disabling just SMBv1 can be tricky. In the “Services” or “Component Services” tool that ships with Windows, the service is just called “Server”. This controls both protocols versions. To get better granularity, you must install a tool, like Sysprog’s SRVMAN, which calls out all of the individual processes. The following is a snapshot showing both protocols in play on a Windows 10 box:
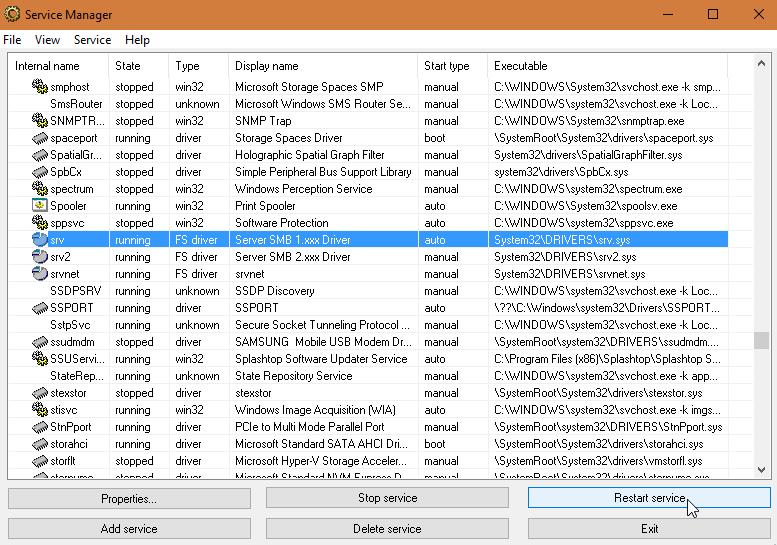
NOTE: It has been my experience that stopping SMBv1 can cause unexpected problems. First off, if you network with any Windows XP boxes, you’re in for trouble. It has no support for SMBv2. Also, many Copiers, Printers, and Network Storage devices use SMBv1 protocol. Connectivity to these devices might be affected as well. Older Linux systems and Android devices *may* use SMBv1 as well. Apple uses SMBv2 with every release starting with OS X 10.7 Lion.