Introduction
In 2014, in response to an Executive Order from President Obama, the National Institute of Standards completed “Framework for Improving Critical Infrastructure Cybersecurity“, also known as “The Cybersecurity Framework“. The framework looks like a “Bow Tie”, from NISTIR 8170:
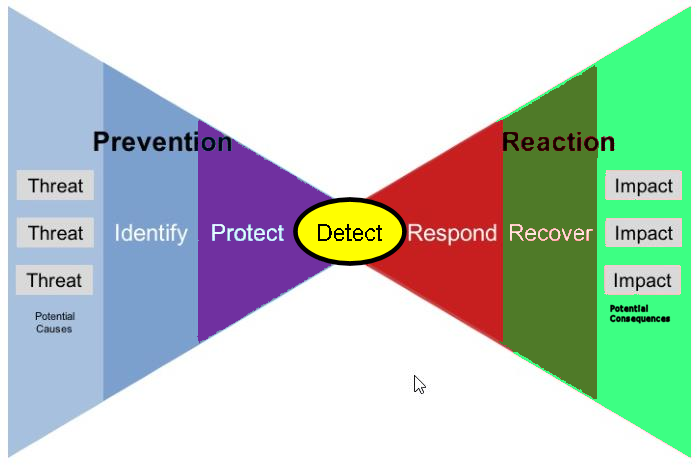
The Framework’s five functional components are:
|
Framework Categories
Again, from NISTIR 8170 the Framework functions are broken down into Categories, Subcategories, and Information References (Polices/Procedures).
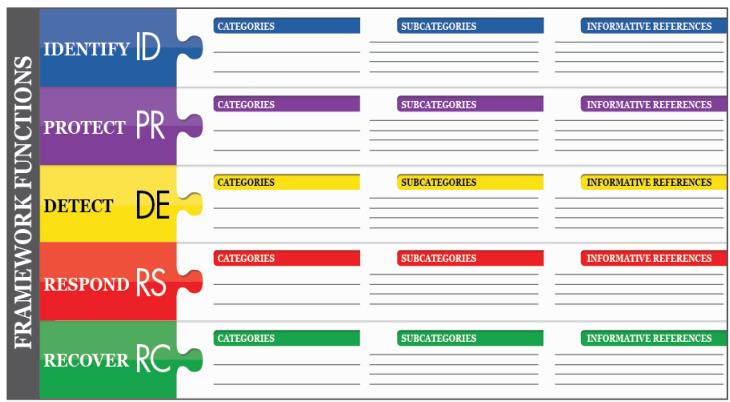
Business Processes
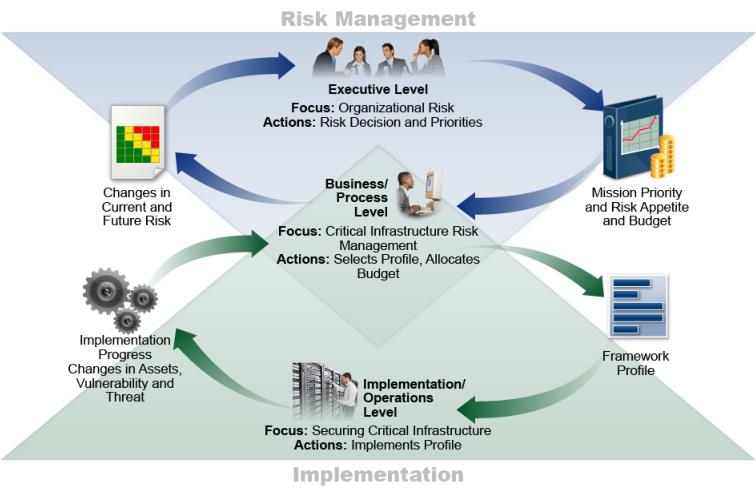
The following diagram is a “notional” representation of Business Process management as it applied to Information Technology. The actual implementation will be tailored to the individual business/entity. From NIST “Framework for Improving Critical Infrastructure Cybersecurity“, February 12, 2014, Version 1.0:
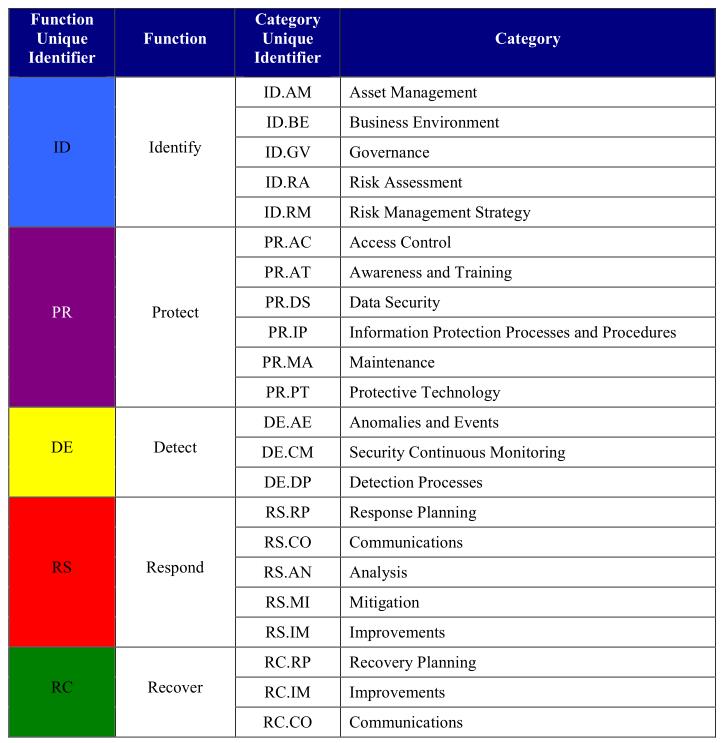
Development of Functional Categories
Finally, we can develop the Categories and Subcategories for each Framework Function. This will depend upon the organization structure of your company. The following example was extracted from NIST “Framework for Improving Critical Infrastructure Cybersecurity“:
- Step 1: Prioritize and Scope. The organization identifies its business/mission objectives and high-level organizational priorities. With this information, the organization makes strategic decisions regarding cybersecurity implementations and determines the scope of systems and assets that support the selected business line or process. The Framework can be adapted to support the different business lines or processes within an organization, which may have different business needs and associated risk tolerance.
- Step 2: Orient. Once the scope of the cybersecurity program has been determined for the business line or process, the organization identifies related systems and assets, regulatory requirements, and overall risk approach. The organization then identifies threats to, and vulnerabilities of, those systems and assets.
- Step 3: Create a Current Profile. The organization develops a Current Profile by indicating which Category and Subcategory outcomes from the Framework Core are currently being achieved.
- Step 4: Conduct a Risk Assessment. This assessment could be guided by the organization’s overall risk management process or previous risk assessment activities. The organization analyzes the operational environment in order to discern the likelihood of a cybersecurity event and the impact that the event could have on the organization. It is important that organizations seek to incorporate emerging risks and threat and vulnerability data to facilitate a robust understanding of the likelihood and impact of cybersecurity events.
- Step 5: Create a Target Profile. The organization creates a Target Profile that focuses on the assessment of the Framework Categories and Subcategories describing the organization’s desired cybersecurity outcomes. Organizations also may develop their own additional Categories and Subcategories to account for unique organizational risks. The organization may also consider influences and requirements of external stakeholders such as sector entities, customers, and business partners when creating a Target Profile.
- Step 6: Determine, Analyze, and Prioritize Gaps. The organization compares the Current Profile and the Target Profile to determine gaps. Next it creates a prioritized action plan to address those gaps that draws upon mission drivers, a cost/benefit analysis, and understanding of risk to achieve the outcomes in the Target Profile. The organization then determines resources necessary to address the gaps. Using Profiles in this manner enables the organization to make informed decisions about cybersecurity activities, supports risk management, and enables the organization to perform cost-effective, targeted improvements.
- Step 7: Implement Action Plan. The organization determines which actions to take in regards to the gaps, if any, identified in the previous step. It then monitors its current cybersecurity practices against the Target Profile. For further guidance, the Framework identifies example Informative References regarding the Categories and Subcategories, but organizations should determine which standards, guidelines, and practices, including those that are sector specific, work best for their needs.
An organization may repeat the steps as needed to continuously assess and improve its
cybersecurity. For instance, organizations may find that more frequent repetition of the orient step improves the quality of risk assessments. Furthermore, organizations may monitor progress through iterative updates to the Current Profile, subsequently comparing the Current Profile to the Target Profile. Organizations may also utilize this process to align their cybersecurity program with their desired Framework Implementation Tier.
Examples
NIST’s The Cybersecurity Framework provides plenty of example charts. I’ve snipped out just a few sections here to indicate what they look like when completed:
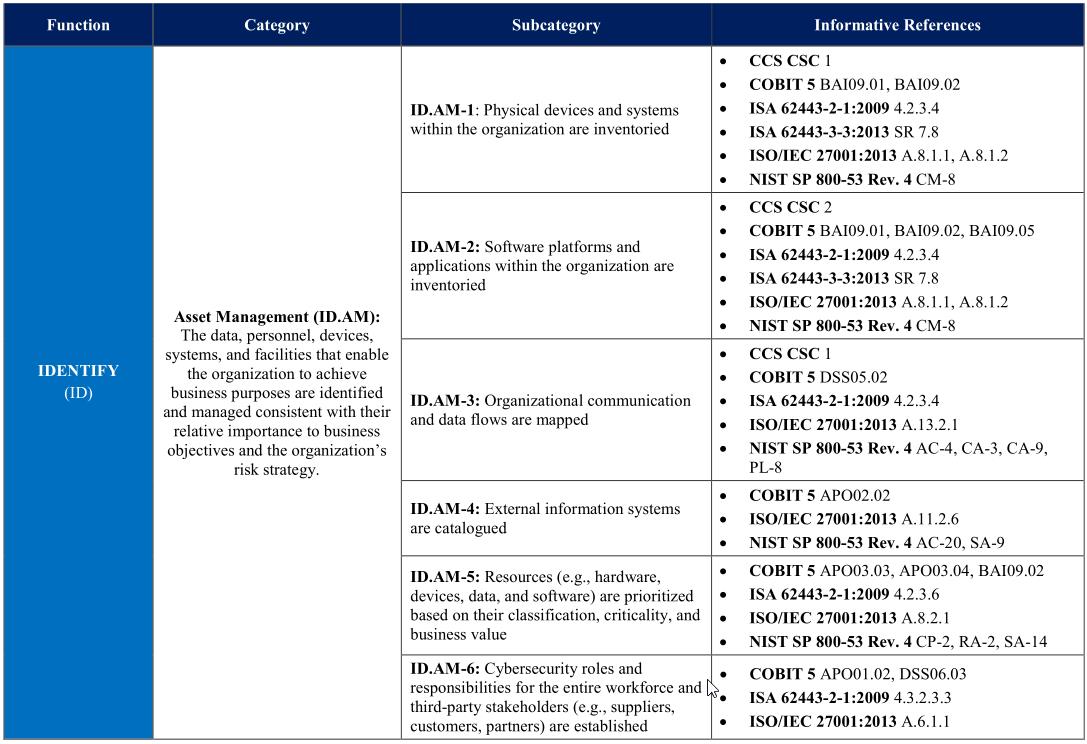
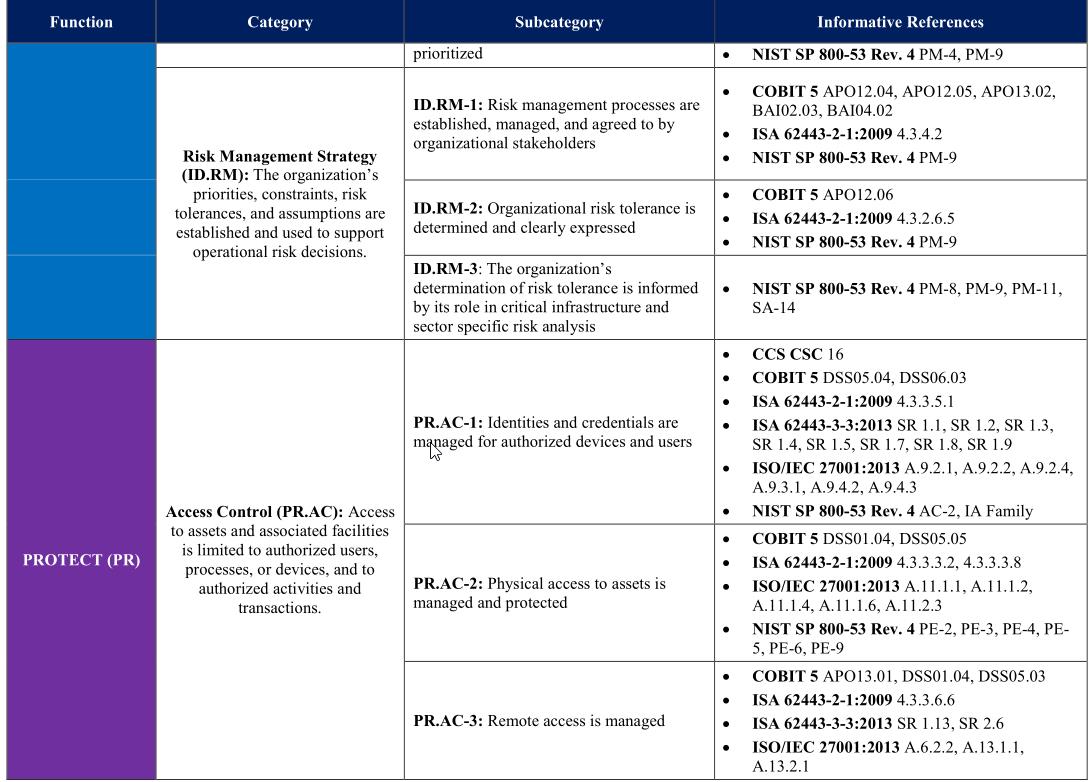
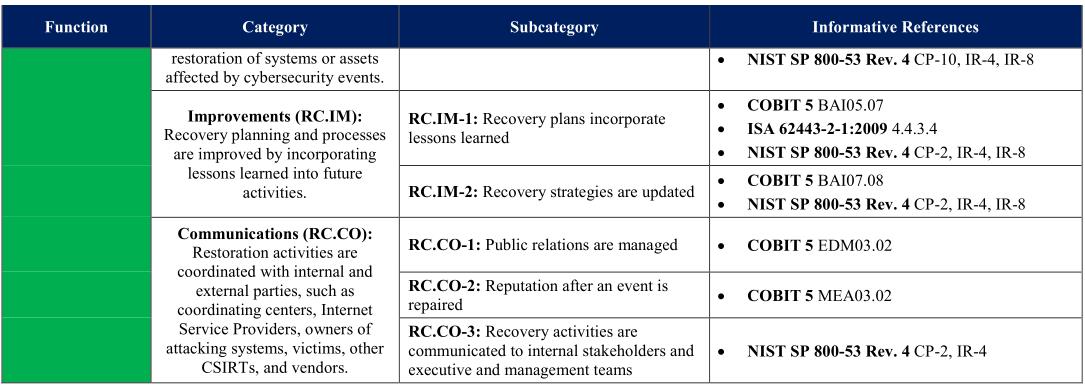
Conclusion
The Cybersecurity Framework is an excellent methodology by which to ensure the adequate checks, balances, and oversight for an organization. It can be adopted by any organization, large or small. Companies can expand this into a more comprehensive IT Operational Framework to include particulars for their line of work. For example, companies requiring PCI/DSS compliance may include auditing of documents with PCI. HIPAA compliant companies may include guidance for managing PHI information. Other companies with High Availability needs may want to factor in things like Load Balancing, Business Continuity services, and Environmental factors, like temperature power, and atmospheric disturbances (lightning, etc.). I shall leave you with a quote:
“Security is a process, not a product”
References
NIST Cybersecurity Website
The Cybersecurity Framework (PDF)
Executive Order no. 13636, February 12, 2013
Cybersecurity Industry Resources
NISTIR 8170 (DRAFT)