Foscam, a Chinese manufacturer of IP Cameras, is a good example of what’s bad with the Internet of Things. They also demonstrate that low-cost *is* low-security. If you have a Foscam product, you might as well put a sign up saying, “Hack Me. I don’t care.”
F-Secure released a report earlier this week detailing critical flaws in the Opticam i5 HD and the Foscam C2 series of products. Despite being notified several months ago of the problems (18 vulnerabilities total), Foscam has not fixed the problems.
- Non-random default credentials for web user interface account
- FTP server account uses empty password
- FTP server account has a hard-coded password
- Configuration back-up file is protected by hard-coded credentials
- Hidden hard-coded credentials for web user interface
- Hidden Telnet functionality
- Remote command injection in User Add
- Remote command injection in /mnt/mtd/boot.sh via ProductConfig.xml
- Unauthenticated Remote Command Injection via Anonymous ONVIF SetDNS
- Incorrect permission assignment for startup script: /mnt/mtd/boot.sh
- Incorrect permission assignment for directory: /mnt/mtd/app
- Administrator Credential Disclosure via Anonymous ONVIF GetStreamUri
- Unauthenticated Reboot via Anonymous ONVIF SystemReboot
- Firewall only protects ports 88 and 443
- Missing restriction of multiple login attempts
- Denial of service of the RTSP video feed
- Unauthenticated Persistent XSS via Anonymous ONVIF SetHostname
- Buffer overflow in ONVIF SetDNS
Foscam cameras are re-branded by other companies under the names:

Foscam camera deployment density:
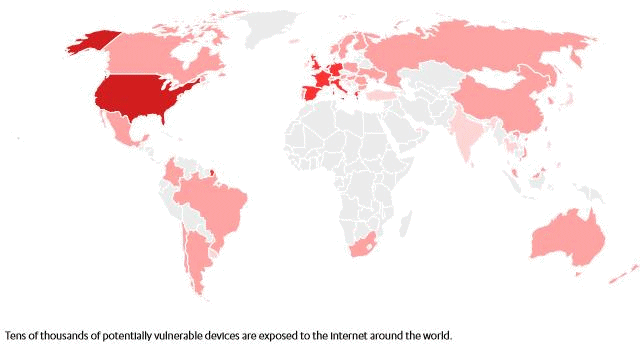
As F-Secure surmises, it is likely that many of these bugs exist in most of Foscam‘s product lines.
F-Secure’s detailed write-up can be found here. A locally cached copy is here.