WordFence issued an advisory about continued Brute-Force login attempts from infected Home Routers. Their original post is here.
This exploit was originally discovered by Checkpoint Software and is called “Misfortune Cookie”. An attacker can send specially crafted HTTP cookies that can alter the router’s system state, tricking the router into treating the session as an “Administrator” session. There are over 200 router models affected, including those from ASUS, D-Link, Edimax, Huawei, TP-Link, ZTE, and ZyXEL, to name a few.
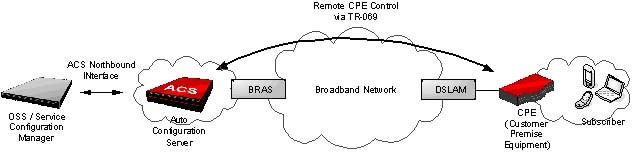
The exploit exists in a chipset Software Development Kit (SDK) provided by AllegroSoft. It provides an embedded webserver called RomPager that normally runs on TCP port 7547. This provides TR-069 CPE WAN Management Protocol (CWMP) functions for telecom carriers. This allows them to provision and manage your device:
WordFence offers a free scan tool so that you can check your router for this vulnerability. If this test fails, it is advisable to turn off your router immediately to flush out any active exploit in progress, then call your phone or cable company immediately.