Wow. That’s a lengthy title that covers just about anything. Really, this is just a sounding-out of what’s been happening in the Spy business lately.
Vulnerability Disclosure
To start with, there’s a good read on Lawfare, entitled “No, the U.S. Government Should Not Disclose All Vulnerabilities in Its Possession“. It was written by Rick Ledgett, Deputy Directory, NSA (2014-2017). He cites the government’s position in not revealing all exploits that they know about. I happen to agree with Rick’s position. So how can a nut-job like Jared take such a position, you ask?
One of the problems that we have with software and hardware bugs is that exploits are a commodity. They are bought and sold to whoever pays the most. Traditionally, that has been the intelligence community (IC). What should happen is that the manufacturers and developers need to come to the table in the common interest of serving their customers. They have competition from the IC for those bugs. But bear in mind that the IC doesn’t just consist of the NSA/CIA. It includes hostile actors from Russia, China, North Korea, Iran, and the rest of the world. What we are seeing now in the free exploit marketplace is increased capital expenditures for bugs by way of Bug-Bounty programs.
As strange as it sounds, it is both fair and balanced. If Microsoft, for instance, doesn’t want hostile actors to exploit SMBv1 bugs (like WannaCry), it needs to come to the marketplace. They are just as responsible as anybody else for the damage that occurred in May 2017. They can no longer rest on their laurels and be silent.
Cyber Command
President Trump has elevated the status of the Cyber Command (aka “CyberCom“) to a unified command. This is analogous to say, US Special Operations Command. CyberCom previously was a sub-unified command overseen by the National Security Agency.
Prior to 2010, the NSA had two components; the NSA and it’s military component, NSA Central Security Service (NSA/CSS). I once generated a cartoon showing the murkiness within the NSA:

In 2009 CyberCom was formed but was brought under the NSA’s jurisdiction in 2010, with the NSA components being NSA, NSA/CSS, and CyberCom. The quasi-civilian/military organization became even more difficult to understand.
The ultimate goal is to allow the military to conduct offensive cyber-attacks and streamline the Command and Control process. However, Cyber Command relies upon the NSA for signals and communications intelligence expertise, while the NSA continues to use the Armed Services for reconnaissance and SIGINT/COMINT data collection purposes.
I am certain that CyberCom can be made self-reliant, but there will be a lot of duplicity with NSA functions. The following diagram lists the current 6 geographic US military commands:
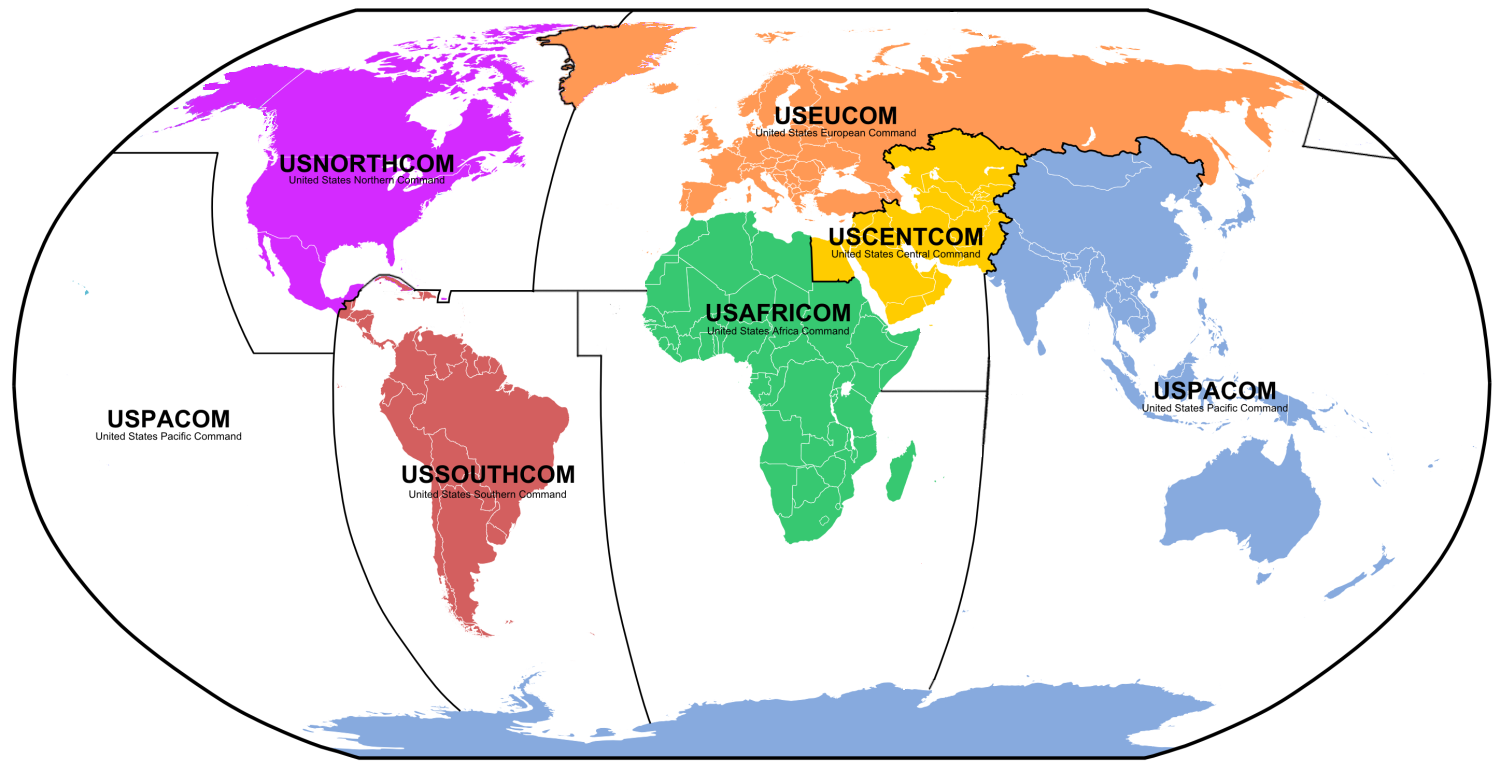
With a projected force of 6,200 people, US Cyber Command becomes one of 4 functional US military commands:
- United States Special Operations Command
- United States Strategic Command
- United States Cyber Command
- United States Transportation Command
At least through 2017 the Cyber Command continues to be headquartered at Ft. Meade, MD, under Admiral Rogers, the Director of NSA.