Perhaps a more apropos title would be: When “Nonce” is not enough! Holy cow, Batman, we’re in for a bumpy ride. The WPA2 protocol is vulnerable to an attack “in-the-wild” called Key Reinstallaton AttaCK (KRACK). This affects both Client devices and Servers (Router/Access Point).
A “Nonce” is a number, usually generated in a pseudo-random fashion and often combined with a timestamp to make it unique through its short-term life-span. It is most often used in Authentication processes. In Cryptographic processes, it is often called an “Initialization Vector” (IV). You certainly don’t want to start off with “0” all the time, as was done in the original WiFi specification, Wireless Encryption Protocol (WEP) with the RC4 cipher.
In fact, it was the introduction of Nonces that created the original WPA2 encryption and authorization scheme called TKIP (Temporal Key Integrity Protocol) using the RC4 cipher. Nowadays, the most common scheme in WPA2 is AES-CCM (Advanced Encryption Standard-Counter with CBC MAC) with some implementations using the newer AES-GCM (Advanced Encryption Standard-Galois Counter Mode).
WPA2 is defined in IEEE 802.11i. Noted cryptographer Matthew Green notes that the real problem with this exploit is the IEEE itself. Standards are commonly formalized in closed-door meetings, and the specifications are impossible to get. He really lights up the IEEE in his post here: https://blog.cryptographyengineering.com/2017/10/16/falling-through-the-kracks/. The IEEE, rightly so, should take the heat. This is a BILLION DOLLAR BLUNDER! Matthew Green wrote a post called “Why I hate CBC-MAC” back in 2013.
By attacking the third message in the Authentication process, an attacker can force key re-installation (same Nonce), or even worse, on Android devices, force the Key to “0”. It is an ill-defined process similar to the work Moxie Marlinspike did with the SSL/TLS protocol. The difference here is that Moxie had access to the RFC standards. Peer-review; it’s a beautiful thing.
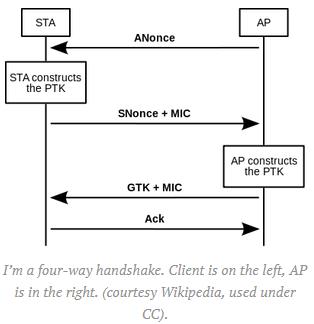
This bug pretty much affects every wireless device on the planet – mobile devices, PCs, Router/Access Points, WiFi cameras and accessories, Wireless Credit Card machines, some sex toys, robots, . Android users, in particular, will be impacted the most due to the lack of timely updates (if any) from the phone companies.
So, here’s the status of fixes:
- Apple: Fixed in IOS, WatchOS, and tvOS. MacOS is still messed up, no date of fix from Apple yet.
- Unix: Patches are available for most systems, especially Debian-based distributions. OpenBSD patched this back in July 2017.
- Android: Google will incorporate fixes in its November Android security updates. No date set for OnHub.
- Microsoft: Fixed on Patch Tuesday 10/10/2017.
- Netgear: Working on fixes, but no dates set.
- Ubiquiti: Updated software available as of today, 10/16/2017.
- Microtik: Fixed in RouterOS v6.39.3, v6.40.4, v6.41rc and later.
- Meraki/Cisco: Fixed with version 24.11 and 25.7 and later.
- Aruba: A fix for ArubaOS is available.
- FortiNet: Version 5.6.1 for FortiAPs is available.
- Cisco: Can be fixed with MR25.7.
- AVM: Will update if necessary. What does that mean?
- DD-WRT: Open-Source router has updated their core base for Devs to use.
- Synology: No fix yet, but in the works.
- WiFi Alliance: Fixes are available for manufacturers; does not cover end-user devices.
I think this problem is going to be with us for a while, particularly with Android and IoT devices. Business networks should have their IoT devices in separate, inaccessible VLANS anyway. This is discussed in my paper, “Life Outside the Firewall”. Access Points and Routers should be updated when new software becomes available for them. WiFi hacks like this require an attacker to be in close proximity to be able to monitor and interfere with the signal. Businesses are the “low-hanging fruit“.
Reference Documents:
- Charged: https://char.gd/blog/2017/wifi-has-been-broken-heres-the-companies-that-have-already-fixed-it
- Matthew Green on KRACK: https://blog.cryptographyengineering.com/2017/10/16/falling-through-the-kracks/
- Matthew Green on hating CBC-MAC, 2013: https://blog.cryptographyengineering.com/2013/02/15/why-i-hate-cbc-mac/
- The Verge: https://www.theverge.com/2017/10/16/16481136/wpa2-wi-fi-krack-vulnerability
- Krackattacks: https://www.krackattacks.com/
- C/NET: https://www.cnet.com/news/if-you-applied-windows-security-updates-youre-safe-from-krack/