Author: Jared Hall
Revision: 1.1
URL: https://www.jaredsec.com/2017/11/08/divorce-esecurity/
Original Date: 11/11/2010
Revision Date: 11/07/2017
Introduction
Separation or divorce is never a good thing. In the case of contested divorces, where the split of assets is complex, the same passion which once brought you and your partner together is often negatively directed to tear each other apart.
This combat-tested IT professional has seen a lot of ugly things during divorce. In today’s world, it is more important than ever to address the Electronic Security threats that occur on the divorce battlefield.
The following guide provides useful insight into some of the challenges you may face. Hopefully, you won’t have any technical hiccups with your breakup. But in the end, a little knowledge goes a long way.
Cordless digital phones
Nobody should use the the analog cordless phones of the 80’s and 90’s. All cordless phones nowadays are digital DECT (Digital Electronic Cordless Telephone).
- Replace the phones and the base-station. An Ex with a suitable phone may monitor your conversations if they are within range.
- Beware of any missing handsets! The range of these phones is generally limited to about 100 feet or so, but I get 200 feet out of mine.
Is your spouse parked on the next block or at the end of your street listening to your phone calls?

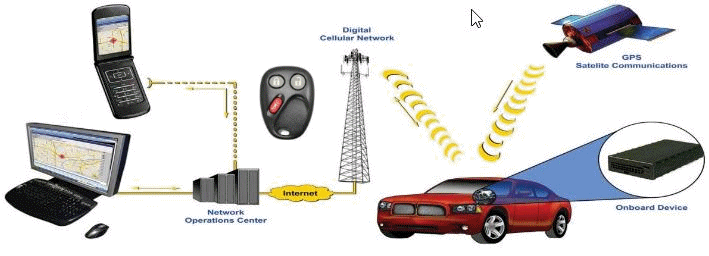
Automobile Telematics
These are you in-car diagnostics and communications systems. Several years ago, you only needed to worry about your Mercedes Benz and their “MBRACE” system. These days, everybody’s got a system, including GM ‘OnStar“, Ford “Sync“, BMW “ConnectDrive“, Chrysler “UConnect Access“, Audi “Audi Connect“, Volkswagon “Hughes Telematics“, Hyundai “Blue Link“, Kia “UVO“, Lexus “Enform“, Honda “HondaLink“, and the Accura “AccuraLine“.
- They all seem to have an App for them.
- Make sure any service subscriptions are in your name.
- Change any “keyless entry‘ system.
- Take your car to the dealer to be sure..l
An estranged spouse can manage your car and track your GPS location with an application on their Smartphone or Tablet. That’s just creepy.
A spouse that keeps track of when you come and go with the kids can get the upper hand in custody battles.
Online Games and Video Rentals
Make sure PlayStation, XBox, and associated online subscriptions (NetFlix, Amazon, etc.) are in your name.
- Change account passwords.
- Change WiFi network passwords.
- Don’t forget about your Smart TV and DVD/Blu-Ray player!
Your Ex shouldn’t know how much playtime the kids have or what movies you rent.

Email Accounts
You’ve had the same Email address forever. What was once so cool and convenient is now a security threat. A spouse that gains access to your account can intercept your Emails with your attorney and derail your plans.
- Setup a new “free” Email account from Gmail, Hotmail, Yahoo, etc. Use this solely for the purpose of communicating with your attorney.
- Change all Email account passwords.
- Change your “Security Question” to something that your Ex-spouse doesn’t know. These are commonly used for password resets. See the section on Knowledge-Based Authentication (KBA) further below.
Keep your Email communications private, especially now.
Knowledge-Based Authentication (KBA)
Knowlege-Based Authentication (KBA) systems are sometimes called “shared secrets”. They are a type of “Out-of-Wallet” (not found in a stolen wallet) Challenge/Response system. KBA is often used to reset passwords for accounts.
- “What is your Mother’s maiden name?” That is a KBA challenge. The presumption is that only you know the answer, but so does your Ex.
- Make a list of all your popular social and business websites that use “shared secrets” for authentication purposes.
- Change the answers to be something different altogether and record your responses in a safe or lockbox. For example, change the answer to “What is your Mother’s maiden name to “Wilma”. Change: “In what city was your high school” to “Bedrock”, “What is your pet’s name” to “Dino”, “What was your first job” to “Quarry Operator“, “Favorite Food” to “Bronto Burger”, etc.
Social Engineering is the #1 way in which an estranged spouse will attack you.
Answering Machines
Does anybody ever change/setup their remote message playback codes? Be smarter than your former spouse!
- Pull out the manual and change the “remote playback” codes.
- Get a new Answering machine..
Do you really want your Ex-spouse to listen to your messages?

PBX/Phone Systems
No smart home would be complete without its own PBX phone system.
- If your system allows remote access, disable that feature This is sometimes called DISA (Direct Inward System Access).
- Disable or restrict any Web-based monitoring of the system.
- Change all passwords associated with the system. Consult with the manufacturer, if necessary.
Keep your nosy ex-spouse out of your personal communications!

Video/Surveillance Cameras
Most surveillance systems today make use of wireless cameras to communicate to the master station. Today’s systems connect right up to the internet to allow monitoring from your work, vacation home, or even your Smartphone.
- Change the wireless encryption password.
- Change all access codes for the cameras and any Digital Video Recorder (DVR).
- Check with the camera vendor or IT consultant, if needed.
Is your creepy Ex-spouse keeping an eye on you right now?

Wireless Computer Networks
Despite wireless encryption for home networks being available for 20 years now, there are those that still run “open” networks. Don’t do that. Lock down your network.
- If your WiFi router doesn’t have WPA or WPA2 security enabled, then turn it on.
- If it does use security, then change the passphrase for your network.
- Consult an IT professional if assistance is needed.
That nondescript car down the street might be monitoring your computer traffic. Even worse, they can be engaged in other nefarious online activity that can be traced back to your account!
Your personal integrity is at stake. Don’t leave the door open!

Computer Security
Your computer should be among the first things you take a look at during, and after, a divorce. It is incredibly important that you lock it down since this is where you’ll be drafting, viewing, and communicating important divorce documents.
Hackers have no gender. In three cases I’ve been involved with over the last ten years, two of the miscreant offenders were women!
- A shared computer with different logins doesn’t cut it.
- Deleting a computer’s login account doesn’t delete files and programs associated with it.
- Inspect keyboard connectors for “inline” hardware keyloggers. These look like small little “adapters” that sit between your keyboard and the computer.
- Scan your computer for viruses and other malware, including software-based keyloggers.
There is no security without physical security.
Keyless Garage/Home Entry
In simpler times, Paul Simon in “50 Ways to Leave Your Lover” penned: “Just drop off the key, Lee.” More apropos today would be, “Change all the locks, Brock“, or “Change all the codes, Mo“.
- If possible, change the access codes for all garage door openers.
- The same applies to keyless entry doors to the residence, if any.
- If you live in a gated community or secured building, make sure you change the entry keys. Consult your Property Manager or Superintendent for assistance.
Physical security is priority #1. Stay safe.

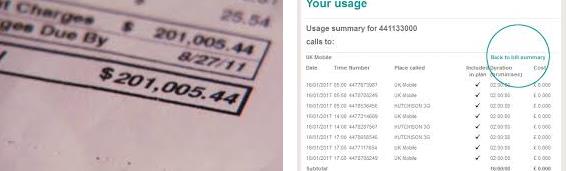
Phone Service
There may be a point in time in which your ex-spouse pays your phone bill. That said:
- Strive to ensure all phone lines are in your name.
- Ensure that “detailed billing” is off,
Your estranged spouse shouldn’t know who you’re talking to.
Cellular/Smart Phones
There are no easy answers here. In this day and age, cell number spoofing is fairly common and can be a big problem if you have a disgruntled ex-spouse or lover.
- Change your Google or Apple ID completely, making sure you’re using a new password as well.
- Change your phone number.
- Consider adding a second phone number (Google voice, for instance).
- Consider disabling GPS/Location tracking.
- Install a Secure Messaging App. If you like communicating with Facebook friends, use WhatsApp. Otherwise use Signal, a drop-in replacement for your phone’s SMS/MMS messaging App.
- Scan the phone for malware, especially if it is an Android phone.
- Consult your phone store or IT professional if you need assistance.
You don’t want your phone to be used against you in a court of law!
Widgets, Gizmos, and Gadgets (WGG)
We all seem to have WGG lying around somewhere. Maybe it is the connected Fridge, Freezer, Crock Pot, Coffee Maker, Thermostat, Oven, Vacuum Robot, Toaster, Smart Picture Frame, or the talking stuffed-bear your Ex gave the kids.
- Change passwords to reflect the new WiFi passwords that you have set.
- Ensure that any web-portals that these devices talk to have their passwords changed also.
- Factory Reset, or thoroughly destroy, any connected “Smart” device or toy before discarding them.
- As for the Talking Bear, keep it at home. Your Ex may suck out your WiFi network password if it ends up in back in “enemy” hands.
- Consider keeping any other connected “Smart Toy” or learning tablet at home.
- Don’t forget about your Home Assistants (Amazon Dot/Echo, Google Home, Microsoft Home Hub).
Inventory, Assess, and Secure your gadgets!
Bugs and Trackers
When things get nasty, and pockets are deep, you may need to worry about your ex-spouse bugging your place or planting a GPS tracker in your vehicle. Life gets very interesting then.
Telephone Bugs/Recorders
- Telephone bugs that built-in radio/RF capabilities can be the size of a USB stick. They can be installed in any indoor jack but are most commonly found in the outdoor “Demarc” box that was installed by the phone company. They have limited range and can’t last too long without running out of power.
- There are telephone line recorders that can be as small as a Mini-SD card. These are usually powered by the phone line itself and have no radio/RF capability. These are installed in the outdoor “Demarc” box where the attacking spouse can gain access and recover, and/or replace, the Mini-SD card.
GPS Trackers/Recorders
- Radio/RF GPS-trackers can be as small as a pack of cigarettes. They constantly receive GPS signals and periodically burst the “data dump” to a cell phone network. Some of these units can dump your GPS coordinates to a nearby WiFi receiver network upon command (drive-by). These are usually attached magnetically to a spot under the bumper or wheel well of your vehicle.
- GPS recorders can vary in size, from as small as a USB stick to the size of a pack of cigarettes. The larger size is most predominate. Trucking, courier, and other transportation drivers are often given these so that management can dump them at the end of the day or route. They require physical access to your vehicle and are often deposited in the glove box or side door pocket.
GPS trackers, because of the need for physical connection to your vehicle can almost always be detected by doing a thorough inspection of your vehicle. A local mechanic can do this for you, if necessary.
Electronic bug detection is a little more complicated. You may be able to go to a local “Spy” store and get a cheap bug sweeper. They usually trigger on signals in the WiFi bands of 2.4 GHz and 5 GHz (5.1 to 5.8 GHz). A more professional approach is to use a device called a Wideband Frequency Selective Voltmeter (FSV). These are manufactured by companies such as Hewlett Packard, Tektronix, Sierra, Cushman, Seimens, Wandel and Goltermann, Rhode & Schwartz, and Telefunken.
If you require the detection of bugs, you’re probably not going to find that level of expertise in your average IT person. You’ll want to solicit help from a Private Investigator with some SIGINT, COMINT, and ELINT experience; a PI who works in the field of “Technical Surveillance Counter-Measures“, or TSCM for short. Some states require, for court evidentiary purposes, that such work be performed by a licensed PI.


