On June 15th, 2017, WikiLeaks provided more “Vault 7” dumps detailing a CIA WiFi router hacking program dubbed “CherryBlossom“. The WikiLeaks dumps can be found here.
CherryBlossom is a WiFi router exploitation program designed by the CIA as part of a larger program, “CherryBomb“. A tool called “Claymore” is used to identify WiFi devices. It then launches tools to exploit two exploits, named “Tomato” and “Surfside“. Once exploited, new firmware is loaded which allows the CIA to monitor router traffic and perform Man-In-The-Middle (MITM) authentication spoofing.
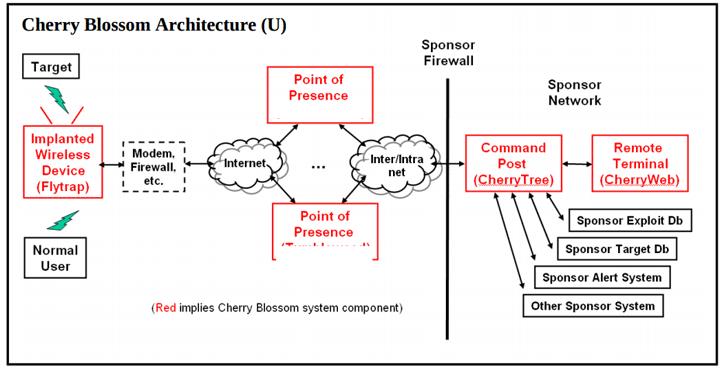
In some cases, special “Beacon” software is installed called “Flytrap“. In the following diagram, “Flytrap” systems appear behind a customer’s firewall and report to C&C (Command and Control) servers called “CherryTree“.
Routers and access points targeted by CherryBlossom
Again, while it’s clear that the CherryBlossom project targeted the following list of routers, it is not clear which have been successfully compromised:
- 3Com: 3CRWE454A72, 3CRWX120695A, 3CRWX275075A, 3CRTRV10075, 3CRWE41196, 3CRWE454G72, 3CRWE53172, 3CRWE554G72T, 3CRWE554G72TU, 3CRWE675075, 3CRWE725075A-US, 3CRWE754G72-A, 3CRWE754G72-B, 3CRWE825075A-US, 3CRWE875075A-US, 3CRWE91096A, 3CRWE91096A, 3CRWE920G73-US, 3CRWEASY96A, 3CRWEASY96A, 3CRWEASYG73-U, 3CRWX440095A
- Accton: WA3101, WA4101, WA5101, WA5201, WA6101, WA6102, WA6102X
- Aironet/Cisco: Aironet 1310 Outdoor Access Point /Bridge, Aironet 350 Series Wireless Bridge, 1300 Series Outdoor Access Point/Bridge, Aironet 1200 Series a/b/g Access Point, Aironet 1310 Outdoor Access Point/Bridge, Aironet 350 Series, Aironet 350 Series AP, Cisco Aironet 1400 Series Wireless Bridge, Cisco Aironet 1400 Series Wireless Bridge
- Allied Telesyn: AT-WA1004G, AT-WA7500, AT-WL2411
- Ambit: (No models specified)
- AMIT, Inc: WIS418, WQS418, WUC128
- ANI Communications: (No models specified)
- Apple: AirPort Express
- Asustek Co: WL-160g, WL-300, WL-300g, WL-330, WL-330g, WL-500b, WL-500g
- Belkin: F5D7230-4
- Breezecom: AP-10, AP-10D, BU-DS.11, BU-DS.11D, DS.5800 Base Unit, RB-DS.11, RB-DS.11D, SA-10, SA-10D, SA-40, SA-40D, WB-10, WB-10D
- Cameo: WLB-2006_2007, WLB-2203/2204, WLG-2002/2003, WLG-2204/2205
- D-Link: AP Manager or D-View SNMP management module?, DCS-2100+, DCS-3220G, DCS-5300G, DCS-5300W, DI-514, DI-524, DI-624, DI-714P+, DI-774, DI-784, DI-824VUP, DP-311P, DP-311U, DPG-2000W, DP-G310, DP-G321, DSM-320, DVC-1100, DWL-1000AP+, DWL-120, DWL-1700AP, DWL-1750, DWL-2100AP, DWL-2200AP, DWL-7000AP, DWL-7100AP, DWL-800AP+, DWL-810+, DWL-G700AP, DWL-G730AP, DWL-G800AP, DWL-G810, DWL-G820
- Epigram: (No models specified)
- Gemtek: WADB-100G, WHAPC-100GE 11G, WHRTC-100GW, WX-1500, WX-1590, WX-1600, WX-1688, WX-2214, WX-2501, WX-5520A, WX-5520G, WX-5525G, WX-5525R, WX-5541, WX-5545, WX-5551, WX-5555, WX-5800, WX-5801, WX-5803
- Global Sun: CM054RT, WL AP 2454 NM0, WL AP 2454 QA0, WL AP 2454 QA3, WL MU 2454 13I0, WL RT 2454 NM0, WL RT 2554 QA0, WL UD 2454 13I0
- Hsing Tech: (No models specified)
- Linksys: BEFW11S4, WAP11, WAP51AB, WAP54G, WAP55AG, WCG200, WET54G, WET54GS5, WGA11B, WGA54G, WMA11B, WMLS11B, WPG12, WPG54G, WPS11, WPS54GU2, WRE54G, WRT54G, WRT54GP2, WRT54GS, WRT55AG, WRV54G, WVC11B, WVC54G
- Motorola: WR850G
- Orinoco: AP-2000 Access Point, AP-2500 Access Point, AP-4000 Tri-Mode Access Point, AP-600 Access Point, Orinoco AP-700, Tsunami MP.11, Tsunami QuickBridge 11, Tsunami QuickBridge 20, Tsunami QuickBridge 60
- Planet Tec: WAP-1963A, WAP-4030, WRT-413, WAP-1963, WAP-1966, WAP-4000, WAP-4050, WAP-5000, WAP-5100, WL-U356, WRT-403, WRT-410
- RPT Int: (No models specified)
- Senao: 5GHz/2.4GHz Dual Band Wireless Access Point, Aries2, Dual Band Wireless Access Point, Long Range Wireless Dongle, Long Range Wireless Outdoor Client Bridge, NL-2511AP PRO PLUS, NL2511SR Plus, NL2511SR Plus(A), NL-2611AP3 PLUS, NL-3054CB3 PLUS, Outdoor Wireless Access Point/Router, Outdoor Wireless Bridge, SL2511SR Plus, Wireless 11g Broadband Router, Wireless Multi-Client Bridge/Access Point
- US Robotics: USR5420, USR5430, USR5450, USR8054
- Z-Com: XG-1100, XG-2000, XG-3020, XG-580, XG-580Plus, XG-581, XG-582, XI-1450, XI-1500, XI-1510
Flytrap routers
Within the CherryBlossom release, there are also documents that appear to target seven specific routers for use with “Flytrap.” Flytrap is a tool CherryBlossom uses to “beacon over the Internet to a Command & Control server referred to as the CherryTree,” according to WikiLeaks.
The CherryBlossom documents included firmware flashing instructions labeled “Flytrap” for each of these router models:
- Belkin: F5D8231
- DLink: DIR130
- Linksys: WRT320N, WRT54G, WRT300N, WRT54GL, WRT54GL
To mitigate manipulation of your access points and routers:
- Make sure your A/P or router’s software CAN be upgraded.
- Upgrade the A/P or router’s software to the current version.
- Ensure strong passwords are used. Never use the router or A/P defaults.
- Disable unused management protocols like SNMP and especially UPNP.