Author: Jared Hall
Revision: 1.3
URL: https://www.jaredsec.com/life-outside-the-firewall-protection/
Date: 06/30/2017
Introduction
Life outside the firewall is a virulent place. Every moment, of every day, your network is being probed, poked, and prodded. I can recall a friend of mine who stopped by the office back in 2004 and built a RedHat Linux box. After five minutes, it was hacked. Hackers exploited a bug that existed in the Secure Shell (SSHD) server component. I read about a recent IoT camera exploit that occurred within 30 seconds of the camera coming online. I’ve lived outside the firewall, and that doesn’t surprise me at all. Life outside the firewall is a war zone.
Your access credentials, e-mail addresses, exploits, and vulnerabilities are all packaged, branded, and bought and sold on the Dark Web. It’s an entirely automated business and there are a lot of participants. In today’s world, your business needs much more than a NAT router (Network Address Translation) to have a fighting chance of survival.
There was a lot of discussion about this following the devastating impact of the WannaCry(pt) ransomware attacks earlier this month, May 2017. I am writing about the best of these security practices; what needs to be done to protect your network.
Treat the Internet Like Sex: Use Protection!
Security is a Compromise
If your business is to survive, without being torn apart or breached, you need to get real paranoid, real fast. I offer you the following pearls of wisdom:
- Distrust and caution are the parents of security. –Benjamin Franklin
- Just because you’re paranoid doesn’t mean they’re not out to get you. –Joe Denney
- Trust no one, believe nothing. –Popular April Fool’s day saying
- Security costs, but so does the lack thereof. –Jared Hall
It is not possible for a single solution to provide adequate protection in today’s hostile Internet environment. I recommend a tiered security solution, as illustrated below:
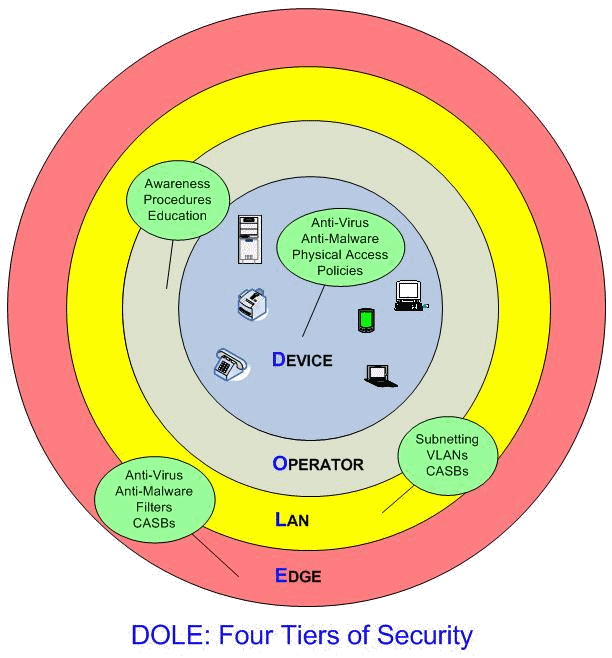
The section titles in the document have been appended to reflect the responsible tier, {D], [O], [L], [E]. It is important to realize that security is a compromise. All systems and networks have flaws! Distrust anybody who says anything different. So, as you read this document:
Take What You Can, Apply What You Can, and Leave The Rest.
Edge-based Malware Protection [E]
Anti-Malware protection needs to be deployed in “tiers”. At the bare minimum, you need it on all of your workstations and servers. And you need it at the “edge”, where your network connects to the Internet.
These boxes are called Security Appliances (SA), Next-Generation FireWalls (NGFW), or Unified Threat Management (UTM) routers. Costs for these products have gone down over the years, but expect to pay $1000 for one, plus another $350/year for Anti-Malware renewal. Get one from a company whose sole focus is on delivering a security product. Here are some reputable vendors (listed from lowest to highest cost):
WatchGuard Technologies, Inc.
WatchGuard started up around 1996. They are based out of Seattle, WA. and are known for the bright red color of their boxes. I’ve always considered them to be good with security, weaker on the networking-side of things. In my opinion, this is a good solution for small businesses.
Fortinet, Inc.
Fortinet emerged from the company “NetScreen” back in 2000. They are based out of Sunnyvale, CA. They are pretty good with both security and networking; and one of the biggest innovators in the market. I would recommend Fortinet products for small and medium-sized businesses. This is one of Jim Cramer’s (“Mad Money“) favorites.
Sophos, Ltd.
An English company, headquarted in Abingdon, UK, Sophos started up as a software antivirus solution back in 1997. Sophos now offers a variety of network devices. I think Sophos has the best cloud integration. I’m happy that they’ve entered this market. I would certainly recommend Sophos for Small to Medium-sized businesses.
Palo Alto Networks, Inc.
This is one of the new guys on the block, starting up in 2005. They are located close to Fortinet in Santa Clara, CA. These guys are good with security and networking. They are the industry’s “darling”, particularly because of their throughput capabilities. This is another one of Jim Cramer’s (“Mad Money“) favorites. I would recommend PAN for medium and Enterprise businesses.
Checkpoint Software Technologies Ltd.
Headquartered in San Carlos, CA, they are located between San Francisco and Santa Clara/San Jose off the “101”. Starting with the timeless “Firewall-1” way back in 1994, Checkpoint is the granddaddy of them all. Another Jim Cramer favorite, Checkpoint continues to drive innovation in the security market. I’d recommend Checkpoint for medium and Enterprise businesses. You won’t be fired for buying Checkpoint.
SonicWall
SonicWall started up in San Jose, CA back in 1991 under the name “Sonic Systems”. They primarily build Ethernet networking products for the Apple marketplace. By the end of the 1990s, the company had a solid, standalone network security appliance called SonicWALL. They renamed the company as such and ultimately went public. Dell acquired the company in 2012 and later sold it off to the private equity firm “Francisco Partners and Elliott Management” in 2016. They do a solid job with network security and are best known for their outstanding VPN client.
Cisco and Juniper Integrated Routers
Both Cisco and Juniper are router and networking companies. I”m a little bit of a purist when it comes to security, preferring a product that is dedicated to the task. However, both of these companies provide complete, integrated networking and security devices. Cisco Systems is headquartered in San Jose, CA, while Juniper Networks is headquartered in nearby Sunnyvale, CA.
If You Want Security, You’ve Got to Protect the Edge.
Computer-Based Malware Protection: Commercial [D]
This as equally important as malware protection at the network edge, if not more so. I recommend good, stout third-party solutions here. Specifically, the following programs in order of most favorable to least favorable:
NOD32 by ESET
NOD32 antivirus is derived from the original NOD software developed in 1987. It is provided by ESET, spol. s r.o., a Czech company that started in 1992. They have a variety of consumer programs and bundles for businesses. Their products are not only effective, but easy to purchase and use. I like this company the most.
GravityZone by Bitdefender
Bitdefender first started up around 1997 in Bucharest, Romania. As such, they are among the newest antivirus companies. They were among the first to offer comprehensive spam detection services and also among the first to incorporate Machine Learning algorithms into their software products. They are also among the leading innovators in this space. They are aggressive in their scanning techniques and are known to have problems with Comodo Firewall and the Nirsoft family of forensic tools. Nevertheless, they are very, very good. I highly recommend them.
Symantec End-Point Protection
Symantec was formed in Mountain View, CA as an Artificial Intelligence company that focused on DEC mini computers. It acquired Peter Norton Computer in 1990 and as such, the venerable Norton Antivirus. Symantec continued to grow and acquire companies, such as PC Tools and Veritas (Backup Exec). Kudos to Symantec for realizing that dilution is not the answer to a security. They spun Veritas off as an independent company again. Symantec has acquired Blue Coat Systems (formerly Cache Flow), so it would appear to have a desire to get into the hardware space. They are the world’s leader and greatest innovator in the software anti-malware space. You won’t get fired for buying Symantec.
If You Wear Big Boy Clothes, Use Big Boy Protection.
Computer-Based Malware Protection: Free [D]
Yes, there are a lot of free anti-virus/malware products out there. Unfortunately, they are *free* in many ways:
- Free of cost
- Free of features
- Free of innovation
- Free of any real value
Except for very small businesses of less than 20 seats, these don’t really belong in your organization. Nothing says “I’m too cheap to care” than a network that is running only on Windows Defender. Really, what is your business worth anyway? Consider that the latest WannaCry(pt) ransomware attack earlier this month (May, 2017) sliced through these like a hot knife through butter. It is even likely that the hacker that developed WannCry(pt) did so on a Windows machine running the standard Windows Defender service. Nevertheless, here are few worthy players in the Free Windows-based anti-virus/malware space:
- Avast
- AVG
- VIPRE
- Microsoft Anti-Malware/Windows Defender
I will say that you can get a decent amount of security by using these programs in association with good anti-spyware/malware programs like Super Anti-Spyware and MalwareBytes.
If you go this route, keep those programs up-to-date by running them every couple of weeks, making sure to get definition updates first. At the first sign of unusual behavior close all browser windows and run a anti-malware scan. Such unusual behavior would include things like missing or added icons on the desktop, unexpected Google/Facebook/Twitter authorization prompts (OAuth), or extreme sluggishness when browsing.
If malware definitions refuse to load, turn off the PC immediately and seek professional computer repair help.
Any Kind of Protection is Better Than Nothing!
Keep The O/S Current [D]
Regarding this month’s May 2017 WannaCry(pt) ransomware outbreak, fully patched Windows 10 systems were not prone to infection from neighboring PCs. Microsoft was late in fixing Windows 7 and 8 until the outbreak was in full-force. However, there is no excuse for not keeping current with Windows Updates.
When reading various other Security blogs, there are always those that pipe up; citing problems they’ve had in the past with Windows Updates. Believe me, I’ve had customers affected by this as well. There was one disturbing update for Windows 7 that caused a boot loop when the update interfered with AVG. This ONLY affected certain ACER machines. Still, I am absolutely certain that if you look at the number of updates delivered, versus the number of problems resulting from bad updates, those negative opinions are the minority. Nobody is perfect, and Microsoft is no different. Move along now.
A big problem that Microsoft has is that, unlike Apple, it doesn’t have much control over the hardware that a user installs. To that end, Microsoft has changed it’s stance over what H/W platforms it does support. Microsoft does not update H/W drivers automatically anymore. You’ll need to use vendor-supplied software, like HP’s Support Assistant, to manage device drivers and keep them current.
Since digital signing is required for drivers, Microsoft does have (at least should have) a vendor’s current driver package on-file at Windows Update. You’ll need to use a third-party tool to identify and download them. I like to use Mister X’s Windows Update MiniTool.
There are those that say, “Vendor XYZ doesn’t support Windows 10….”. I was particularly dismayed with the UK’s NHS after the WannaCry(pt) outbreak. You would figure that a monopolized, single, mammoth customer would have some clout with their EMR vendors. I’m sure they do; they just didn’t exercise it. If you are such a customer that relies on such software relics, write a letter to the vendor’s CEO asking when they will support Windows XYZ. Save their response for subsequent lawsuits. Do not be afraid of change. The math is easy. What have you got to lose (your total business value) versus the cost of changing to another software platform.
There is no Excuse for Not Keeping Current With Windows Updates. Ever.
Backup, Backup, Backup [D]
You need to have a backup solution. The easiest way to go is with a simple backup USB drive connected to your computer. Once attached, the Windows “shell” will render the drive in the list of available devices when you click on the “My Computer” or “This PC” icon in the Start Menu or from File Explorer. Simply copy your files over to the backup drive.
Back in October 2016, I spent a couple of days decrypting files on a individual’s PC and backup drive; a little bit over a Terabyte all told. Since ransomware and other viruses will infect the drive with impunity, disconnect and safely store the backup drive when the backup job is complete.
If you use a cloud backup service you need to be concerned with how it integrates to your computer. Many services just appear as icons or drives to your computer. This is the Windows “shell” making it easy for you to get your stuff. Unfortunately, it makes it easy for a hacker to get your stuff also.
When working with online backup services, select a plan that supports versioning. I’ve seen cryptoviruses encrypt user folders on the regular Carbonite plan. Upgrade to the Carbonite Pro to preserve older versions of files. That way if your files get encrypted, the older, correct, version will be preserved.
For pure-play (manual “one-and-done“) backups, I recommend using Mega.nz. Mega was started as a legitimate site after the takedown of Kim Dotcom‘s DCMA-impinging, file-sharing service called “MegaDownload“. The free version will suffice for many, while the business options are very good. They have a keen eye for security also. As they are out-of-country, it is a little more difficult for US security entities to get to. Files are encrypted with AES-256, and only you have the key.
As the cost of NAS (Network Attached Storage) boxes get cheaper, you should consider purchasing one and “image” select computers. When a disk image is preserved, it is easy to recreate that entire computer from scratch; right down to the individual drivers, files, and settings. The granddaddy of them all is probably “Drobo“, but “Synology“, “QNAP“, and “Netgear” all make great NAS servers.
Look at your backups at least once a week. Hackers, once they’ve gained entrance to your network, do scans and seek out backup locations and file shares. Those are usually the first to be breached or encrypted. After all, the hackers know that if you can recover from backup, a ransom demand is useless.
Happiness is Knowing Your Data is Backed Up!
Minimize Your Footprint [E]
You want to keep your company’s public IP address(es) as secret as possible. To effectively reduce your exposure it is necessary to minimize your Internet footprint.
- Block Pings: This is an easy option to turn on in almost all routers, even the most basic ones. Sometimes this parameter is know as “Block WAN requests”. In days of old, this was very effective. In today’s world it has less value. When I scan networks, I hit the checkbox “Bypass Ping”. So do most hackers with clue. Still, it is a good place to start.
- Outsource Public Services: This means put your Web services and Email services out of your internal network. These services are always targeted for exploitation. Get them out of your internal network.
- Restrict Access to Internal Resources: If you need to run Extranet services that require strategic partners to access Internal resources, implement restrictions based upon the incoming IP address. For example, if your region is served by a few broadband cable companies and carriers, get their Network Blocks (NetBlocks) and only allow access from those IP addresses. A good “whois” client can not only resolve domain and host names, but return netblock (IP address ownership) information as well.
- Use Cloaking: Enable this if possible for Web and Email services. Send yourself an Email and look at the message headers. If your WAN/Internet IP address is listed in there, contact your Email service provider and see about disabling the listing of client IP addresses in email messages. Not all systems support that feature. You may be able to use your Service Partner’s proxy server for cloaking your, or your company’s, source IP address in web (http) requests.
Minimize Your Network Exposure.
Awareness and Vigilance [O]
There is no substitute for “Users with clue”. You must constantly monitor and examine any unsafe Email and Web browsing habits that you and your employees might have. The follow graphic is a breakdown of how malware gets delivered:
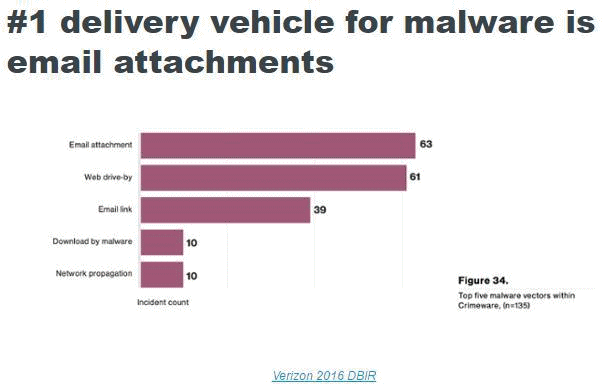
+ Safe Surfing
Everybody uses the Google search engine these days. For the most part, Google does a pretty good job at vetting hyperlinked search results. But “pretty good” ≠ “perfect”. If you have to go past a couple of pages to find what you’re looking for, there is significant risk. There are many methods in which your web browser can get infected. If not through a web page owned by a hacker, then by advertising frames whose content was not vetted by the site owner.
I had a partner named “Big Bill”. He was the kind of guy that would go around and set people’s home pages up to the “Drudge Report“. Yet his workstation was always getting infected. The problem was that hackers had gained limited control of, the SQL database servers used by popular Ad Brokers; namely Yahoo’s Yield Manager and Fox Audience Network’s Fimserve.com. There were infections on a much smaller scale by DoubleClick and MySpace. Despite Google using DoubleClick, they came away clean. They coined the term “Malvertising”, and have policies regarding that here.
Since all bad things start with a stub program called a “downloader“, these types of infections are called “Drive-By Downloads“. Ad content is a little more distributed now, and SQL-Injection attacks are very common today.
You, and every one of your employees need to be educated on this topic. Look carefully at the hyperlinks that are presented to you to visit. If you hover the mouse pointer over the link, you’ll see the URL displayed in the lower-left of web browser. Read the link carefully, so that you have an idea where you’ll be going. If it looks the least bit “sketchy“, then don’t click on the link. Do not trust or assume that your antivirus or Edge security device will protect you.
Even better, once you get past Google’s second page, stop. Point your browser to Bing and do your search there.
+ Email Trickery and Phishing
The most important thing to know now is how to detect:
- Phishing Attacks: Broad-based Email attacks containing content that tricks the unknowing user into installing malware. These are quite often the “Miracle Cure”, “Amazing Trick”, “Simple Tips”, Celebrity scandals, or Sex Tape Emails.
- Spear-Phishing Attacks: These are like Phishing Attacks, only very targeted. They might appear to be from valid friends, business partners, or your bank. Many fall prey to the urgent Email from the company President or CEO. Don’t click on random “invoices” or “scanned documents”. You’ll do your body good.
+ Tidbits of useful information
- The lifespan of a phishing attack is between 62 and 196 hours
- The first sucker bites about 82 seconds after the attack is launched
- A whopping 30% of phishing email are opened by the recipients
- 1/3 of all companies report executives that fell prey to CEO phishes
- Email is the largest medium for the distribution of malware
- 9 out of 10 phishing emails contain Ransomware
- Young adults, 18-25 are the most susceptible, followed by over-65 seniors
- Women are more susceptible than men
- 85 percent of organizations are hit by phishing attacks each year
- HIPAA entities must now report Ransomware attacks as breaches
- Florida leads the US in phishing victims
- Russia generates the most phishing attacks
- Russia hosts the most servers that push malware (The US is #2)
The following graphic shows that across all business sectors, the majority of infections come from Office documents. If you don’t need to send Office documents via Email, then you shouldn’t.
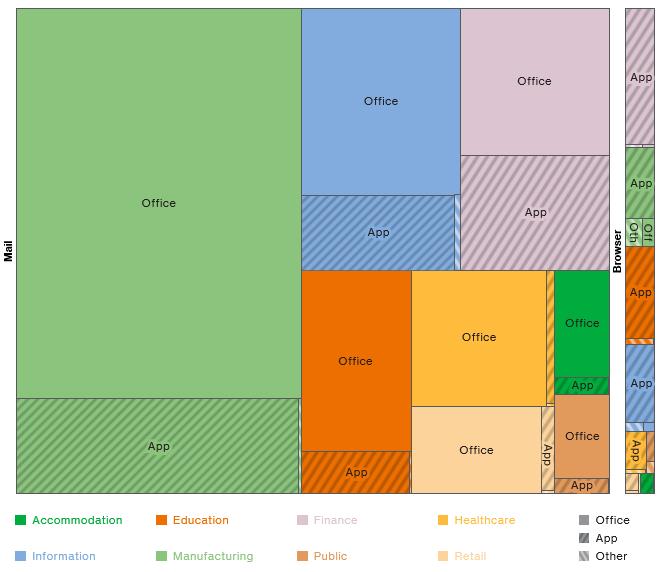
Do Not Blindly Trust Office Documents Sent From External Parties.
Here are a few useful links:
- Why People Click on Things They Shouldn’t
- The Staggering Number of Phishing Victims
- Phishing by the Numbers: 2016
- 2013 Cybercrime Statistics: You Should be Scared
- The State of Phishing Attacks (2012)
- Verizon 2017 Data Breach Investigations Report (Local cached copy)
- Understanding Romance Scams
Awareness Training [O]
Just as you and your kids need training before they can drive, the same holds true for your employees that use your Internet connection. They need to know as much information as possible to stay safe online.
+ Email Message Headers
You, and every employee that has access to email needs to understand how to read Email Messages. All Internet email has Message Headers and Envelope Headers. A Message Header is what is typically displayed to the user; From Somebody, To Somebody. These don’t need to be spoofed at all. You can make these display anything you’d like. The Envelope Headers contain the real meat-and-potatoes. This is the mail server to mail server communication information that is necessary for processing emails. It is, in fact, the Envelope Headers that allow things like Blind Copies to even exist.
You must know how to interpret these headers. The information is presented to the user. The user must do their part in learning their EMail system. This is an important part to detect phishing emails.
Useful Online Phishing Tests, c/o Kim Komando:
http://www.komando.com/happening-now/389720/look-out-for-this-new-tax-season-phishing-scam
http://www.komando.com/happening-now/393678/old-google-login-phishing-scam-is-still-fooling-people
http://www.komando.com/happening-now/392257/can-you-spot-the-problems-with-this-netflix-scam
http://www.komando.com/tips/361345/can-you-spot-a-fake-email-take-our-phishing-iq-test
Training Sites
+ Social Engineering
I can’t say enough about Social Engineering exploits. These appear to be from Telecom companies, IT partners, Strategic business partners, and what not. They are often delivered by a phone call or even in person. “Just click on this link to install our software”. Or a phone call from your “IT Staff” asking you to fill out this form so that you can comply with the new password complexity rules, or what have you.

Facebook is a wealth of information for scammers and other miscreants. It is largely a site powered by nothing but vanity. I’ve seen customers at the Grocery Store become instant Facebook friends, neither one really understanding that not only *should* they worry about their newfound Facebook friend, but also their that person’s relatives, friends, kids, spouses, and whoever else happens to use that *friend’s* computer. Pity the poor wife who posts that “hubby” is off on his third-tour in Iraq. In the hands of a miscreant “Facebook Friend“, nothing good will come from that.
But, as recent analysis of the mass deployment of malware installed on the phones of Israeli soldiers indicate, it’s not just the wives that are at risk. Alas, few people vet their social media friends, and that puts you and your business at risk. Let’s see, suppose I walk into a business, introduce myself as a friend (from what’s listed on Facebook) to the receptionist and write a note: “Woody, here is a cool page where I’ve been putting my stuff. www.getinfected.com. Thanks, Jeremy”. “Can you pass this on to him when you get a chance?” The odds are good that the receptionist will give Woody that note. The odds are good that Woody will get himself infected. Worst case scenario? I get chased of the premises by Woody. He’s too busy to file a police report and it would just look stupid. So I, the hacker, just moves on to the next business victim.
Minimize Your Social Footprint.
Check External Dependencies [O]
We all seem to have external dependencies. You know, Control Panels, Domain Name Registrars, DNS Managers, Site Configurators, etc. These are most often “set and forget” functions. And while we forget about them, hackers don’t.
When a hacker can manipulate these functions, you are in for a world of hurt. If your domain name or DNS server or records are changed, then a breech is imminent. Your website can be changed to a site that doles out pornography or malware. Inbound emails to you can be sent to another server where they are analyzed and the sender’s emails harvested for spam or spear-phishing attacks; in your name, no less. The damage to you and your comany’s reputation can be devestating.
- Keep your domain name(s) up to date.
- Test the login functions to the external resources. Try entering bogus username and passwords every few seconds. Make sure you, as the administrator, get a notification message of these unauthorized login attempts.
- Keep your domain registration details private (usually an extra charge applies).
- If you run your own DNS servers, watch out fo DNS record exfiltration. If your DNS vendor is external, demand security reports of DNS exfiltration and exploitation attempts.
Your Security is Only as Strong as the Weakest Link.
Physical Access Controls and Policies [O]
Back in the early 2000’s my partner (Big Bill) and I worked a problem with a customer named Baytech Label. They were an integrated Voice/Data T-1 customer. We were the data partner of a local CLEC named KMC Telecom. On day #4 of the end-user’s outage, there was still nothing but finger pointing going on between between Verizon and KMC.
So Bill and I drive down to KMC Telecom. We go over loopbacks through their gear, and then the remote channel from Verizon’s serving Central Office. It was two-wire T-!, on HDSL2+. The customer premises had no signal. We knew where Verizon’s serving CO was, so we went to pay them a visit. “Good luck with that”, quipped one of the KMC Telecom switch techs.
So, we arrived at the nondescript Verizon blockhouse CO, and banged on the metal door until finally it opened and a head peeked out. We announced ourselves as being from KMC Telecom, and wanted to review the circuit ID blah,blah,blah (we presented the valid Interconnect and Verizon circuit IDs). They let us in with only the most casual glances of our photo IDs. The Verizon tech escorted us to their T-1 Patch Panel, where indeed, we found no signal. “See, we tested at the Main (frame) to the premises and it is good”.
At that point, we get interrupted by the other Verizon tech who said, “My boss wants to talk to you.” So, I went to phone and was so informed, “I know you’re not from KMC, so who exactly are you, and what do you want?” I explained that we were from WebNet, KMC’s data partner, and were trying to break the log jam of troubleshooting. He seemed to know who I was, and said, “I”ll give you five minutes, then I’m going to have my guys throw you outside the door. And I mean, they will throw you. OK, let me talk to my tech”. So, I went back to the T-1 patch panel and Bill asked our escort what was between the Main Frame and this patch panel. “Nothing but our IDF (Intermediate Distribution Frame)”, he said. Bill asked “Have you tested from there?” “No”, was the reply, “there’s no labeling on the frame”. So we put on a Warbler and asked the tech if he could find it on the IDF. He went around the back of the frame with Bill’s test wand, and after about a minute said, “Hey, guys, I can see the problem. Any of you boys have a wire-wrap tool?” I had one, gave it to the Verizon tech. Seconds later I got a phone call from KMC Telecom that the circuit was up. I had just put the tool in my bag when the second tech came by and pushed us to the door. Our five minutes was up.
This was clearly a “white-hat” job. Ultimately, Verizon’s access controls kicked in. The location, scope of duties, and duration were clearly defined to minimize threats. Verizon was happy that the problem was closed. KMC Telecom was elated. Baytech Label was as happy as a customer with 4 days of downtime could be, I suppose.
This is an interesting story. You should not be surprised at all that there are thousands of miscreants out there that know you have a Copy machine. They know you have a Telecom Room. They probably know what Phone company you use (easy to do a query to find out who is serving your phone number). They probably know what Internet services you have. When somebody comes knocking, be it a “phone guy”, “copier guy”, “insurance rep”, “drug rep”, “painter”, “IT guy”, what will you or your employees do?

Before you let any visitor plunk down in front of a computer, have them sign an Access Policy every time. Fortunately, there’s some nice Android tablets that will do this for you. Maybe these people are hackers. Maybe they just need to make an extra buck by planting some Ransomware. Maybe they are just having a bad day. Their access needs to be monitored, via surveillance camera or human supervisor. This is a risk of the worst kind, an Internal threat.
Nobody is Who They Say They Are. Trust no One.
Use VLANs For Isolation [L]
OK. For a quick primer, an Ethernet Hub from days of old, takes in an Ethernet frame and broadcasts it all the other Ethernet ports. It is very basic and very easy. With a standard Hub, when Device “A” is sending massive amounts of data to Device “B”, then Device “C” will appear to be slow.
Now we put in an Ethernet switch. When first powered up, it acts just like a switch. But within seconds it learns about what devices are connected to what switch ports. So, it makes things more efficient. A lot of traffic that appears between any two ports does not appear on the other switch ports. Device “A” and Device “B” can send all the traffic they want without affecting Device “C”. But Ethernet broadcasts are still received on all ports. This is called a “Broadcast Domain”.
However, you may wish to further isolate Broadcast traffic, or segment your network such that only certain devices can communicate with each other. To do this, you need to implement Virtual LANs, or VLANs, for short. VLANs always have a numerical identifier associated with them. This is a number from 1 to 4094. If you look at the math, there is a 12-bit Tag (4096). But 0 and 4095 are not used.
In reality, the number of VLANs you have to play with will be limited by the switch that is used. It is rare to find Ethernet switches that will let you use values greater than 256, and most are even lower than that. You’ll pay a couple of hundred bucks more for a VLAN-capable Ethernet Switch than the ordinary, run-of-the-mill Switch. Sometimes these are called “Managed Switches“.
So, VLANs are great to create Broadcast-Isolated Domains. You might want to put your Guest WiFi system in one VLAN. You might want to put your servers in another VLAN. Network Printers might go into another VLAN.
It would certainly be a good idea to put your IoT (Internet of Things) devices into another VLANs. VLANs for IP Cameras should be setup such that only designated workstations and NVRs are in that same VLAN. Keep everyone else out. The same applies to Entry controls such as door locks or garage door openers. Power controls, Lighting, and Climate controls should be their own isolated VLANs also.
Managed Switches Cost More, But They Buy A Lot!
The Internet of Things [D]
Welcome to the wild world of IoT! This has a pretty broad scope, including devices such as IP Cameras, Entry controls, Climate controls, Power controls, Lighting controls, Small and Large Appliances, Exercise equipment, Even handheld devices, like personal sex toys have wireless capabilities in them. You should expect IoT devices to be inherently insecure. How much money is a manufacturer going to throw into your Crock Pot, Toaster, or Thermostat?
♠ For IoT devices that only need connectivity within the Local Network, use static IP addresses for the devices *and* do not set a default gateway on the device. This will curb the device’s ability to hit the Internet. They can only be managed or accessed by devices within the same local IP subnet.
♠ Use a VLAN for these devices to isolate them from other devices or computers on the Local Network.
♠ In a business environment where IoT devices may belong on the network, program your intelligent router, NGFW, or UTM to restrict and filter Internet access.
♠ Always change the default password of any IoT device. The Manufacturer knows what they are. You know what they are. The hackers know what they are. Studies show that 15% of all people do not change their IoT default passwords. Here’s a listing of frequently used Login defaults for IoT devices. Imagine: from zero to root in 60 seconds! Most of these Username/Password pairs were derived from the Mirai botnet (scanner.c) and its dormant botnet cousin, Hajime:
| 666666 666666 888888 888888 admin (none) admin 0 admin 1111 admin 1111111 admin 1234 admin 12345 admin 123456 admin 54321 admin 888888 admin 7ujMko0admin admin admin admin admin1234 admin meinsm admin pass admin password admin smcadmin admin1 password administrator 1234 Administrator admin |
guest 12345 guest guest root (none) root 0 root 1111 root 1234 root 12345 root 123456 root 54321 root 666666 root 7ujMko0admin root 7ujMko0vizxv root 888888 root admin root anko root default root dreambox root hi3518 root ikwb root juantech root jvbzd |
root klv123 root klv1234 root pass root password root realtek root root root system root user root vizxv root xc3511 root xmhdipc root zlxx. root Zte521 service service supervisor supervisor support support tech tech ubnt ubnt user user |
♠ Check for open management ports. Do a quick port scan of the device. Check for TCP connectivity to ports 20, 21, 22, 80, 88, 443, 8000, and 8080. Manufacturers don’t always close all the doors when the product goes out for shipping. This has been particularly evident with all of the problems coming from Chinese video camera manufacturers, like Huawei and Foscam.
Expect IoT Devices to be Insecure.
TCP/IP Filtering [E]
If you have some intelligence in your router, Next Generation FireWall, Security Applicance, or Unified Threat Manager, use TCP/IP filtering prolifically.
+ Domain Blocking
Block miscreant domains that your users should not be connecting to. This is most useful when applied to Top Level Domains (TLD). For example, domains within the .top TLD are notorious for being used by hackers. Some TLDs that should should be blocked in both Inbound and Outbound directions:
|
|
|
|
+ Postfix Email Server Domain Blocking
For administrators of the Postfix EMail server, create a file called “tld.pcre” in your Postfix configuration directory (usually /etc/postfix). Paste the following into the file:
/\.(info|kr|my|ng|eu|asia|rocks|club|click|website|space|home|xyz|top|work|democ
rat|science|qq|cricket|ninja|digital|webcam|party|review|faith|date|uno|download
|win|wang|accountant|bid|pro|red|trade|loan|site|press|online|ml|gg|gdn|link|mob
i|tk|pw|me|email|kim|gbl|men|stream|love|black|blue|fyi|email)$/i REJECT We do n
ot interchange mail with .$1 domains
In the main.cf file, append the following to the directive “smtpd_recipient_restrictions”:
pcre:/etc/postfix/tld.pcre
In the main.cf file, add or modify the directive “smtpd_sender_restrictions” as such:
pcre:/etc/postfix/tld.pcre
Of course, your Postfix must have PCRE (PERL Compatible Regular Expressions) enabled. Postfix will reject emails received from, or sent to, these TLDs.
+ HTTP and FTP File Extension Blocking
It is also necessary to block dangerous filename extensions that may be sent from, or received by, users with the HTTP or FTP protocols. Some examples include:
|
|
|
|
+ Postfix Email Server File Extension Blocking
For administrators of the Postfix EMail server, create a file called “mime_header_checks.pcre ” in your Postfix configuration directory (usually /etc/postfix). Paste the following into the file:
/^\s*Content-(Disposition|Type).*name\s*=\s*"?(.+\.(ad[ep]|asd|ba[st]|chm|cmd|cpl|crt|dbx|dll|exe|hlp|hta|in[fs]|isp|js|jse|lnk|md[etw]|ms[cipt]|nws|ocx|ops|pcd|pi|pif|prf|reg|scf|scr|sct|sh[bms]|swf|uue|vb|vb[esx]|vxd|wab|ws[cfh]))"?\s*$/ REJECT Files attached to emails that contain or end in "$3" are prohibited on this server as they may contain viruses. The file named "$2" was rejected.
For those with a keen eye, you’ll notice we block a few more extensions here; like .exe, .msi, and .js files. These might be valid on the Web, but have no place in Emails.
Now, in your main.cf file, append the following to the “mime_header_checks” directive:
pcre:/etc/postfix/mime_header_checks.pcre
Use Filtering to prevent hacks before they start!
Protocols and Address Filters [E]
Again, if you have some intelligent router, Next Generation Firewall, Security Appliance, or Unified Threat Manager, some additional filtering is prudent. Make a protocol map of your network; list what protocols are used and why.
+ Block RFC 1918 Private IP Space on the WAN
There are actually a lot of reserved IP address ranges. One of my personal favorites is the old 169.254.0.0/16 network. Your PC will get an address like that when DHCP isn’t working right! And of course, there’s the Loopback Network (“Link-Local“) of: 127.0.0.0/8
Of interest to most people on the planet are the address ranges reserved for “Private-Use Networks“. This is what most IPv4 LAN networks use. They are:
- 192.168.0.0/16 – (Netmask 255.255.0.0)
- 10.0.0.0/8 – (Netmask 255.0.0.0)
- 172.16.0.0/12 – (Netmask 255.240.0.0)
In your router, there should be filters applied both Inbound and Outbound to prevent these addresses from appearing on your WAN/Internet port(s). You might be asking yourself, “They are non-routable. What harm can they do?” Simple. A Carrier’s Cable or Fiber-Optic Entertainment network usually operates in a “Bridged-Mode“. Other entities, even miscreants, that are on your same Bridge can send packets your way; no routing needed.
If you send your LAN network packets out the WAN port, you risk exposing your local network addressing scheme to miscreants that might pick that up. I don’t know about you, but every now again I”ll type something wrong into a web browser and end up with a cable modem’s Web page. That’s when you know you’re on an “el-cheapo” router.
Incoming packets from the WAN are deposited into a big buffer. They can be routed elsewhere or NAT’ed back into the local network. Are you absolutely positive that your router is going to do the right thing and drop those packets? Did you test it?
There was a cable service engineer that told me that this couldn’t happen in *their* network. I chuckled and told her: “Well, maybe your network’s stressed out or just having a Bad-Upgrade Day!”
+ Block File and Print Sharing on the WAN
There is no good reason for Server Message Block (SMB) packets to go into, or out of, your router’s WAN/Internet port(s). There have been some recent exploits with the Chrome browser that allows Windows Shortcut Files (.scf) in. And the target machine will dutifully respond. This should never occur.
Block TCP ports 139 and 445 on your WAN/Internet ports, both Inbound and Outbound. Only bad things will happen if this isn’t done!
+ Get a Grip on the Cloud
Every single company needs to have a Cloud policy that states what employees can and cannot do with external Internet services. There are a couple of simple things to consider: 1) Don’t put stuff in the Cloud that you can’t afford to be lost or exposed and 2) where there is no physical security, there is no security. That has to get weighed with the convenience factor of the Cloud or, if you’re big enough, the cost savings of the Cloud. A study conducted by SpiderOak in january 2017 indicated that 76.8% of the workforce uses unsanctioned applications. This is known as “Shadow IT” and can significantly increase a company’s risk and exposure.
For those entities that use Cloud services, they should be some type of Cloud Access Security Broker (CASB) in place to manage security and Intellectual Property. For small businesses, many of the the intelligent routers/security devices available have filters that control access to Cloud resources.
Large organizations that have extensive DevOps, Storage, or cloud computing needs, are likely going to need more protection than a security appliance/device can provide. The same holds true for those entities who need to control Shadow IT resources.
Filter Unused Ports, Addresses, and Protocols. Believe Nothing.